A trade group representing at least 22 automakers and other original equipment providers are still fighting against Massachusetts' recently passed right to repair referendum. That law not only reaffirmed and updated a 2013 right-to-repair law, but it also added a common method of accessing over-the-air telematics data. Now, the car companies are fighting back.
On Monday, the group began its testimony in front of a federal judge in an attempt to block the referendum. Its argument states permitting consumers and independent repair shops to wirelessly access telematics data from their vehicles would conflict with federal laws pertaining to emissions regulations.

Before we get too deep in the water, let's recap the existing legislation, the proposed changes, and just how automakers have escalated a constituent-approved change to the courts.
What Changed?
The referendum updates Massachusetts' existing right-to-repair act, which went into effect in 2013 and forced automakers to adopt a national right-to-repair standard.
Specifically, the referendum modernizes the law to include a standard method of accessing over-the-air data, the same real-time information that automakers receive when connected cars phone home. This is similar to, say, an OBDII reader, except it's aimed at allowing individuals and small repair shops to have access to the same diagnostic data as automakers, despite being unaffiliated with a particular dealer network.
In November, poll-going Massachusetts residents overwhelmingly voted to approve the referendum. Nearly 2.6 million voters—or 75 percent—voted in favor of the vehicle data access requirement initiative.
The amendment to the law means that automakers who want to do business in Massachusetts are required to make this telematics data accessible through a smartphone app beginning with model year 2022 and newer vehicles. For some automakers like Honda, MY2022 vehicles were already on dealer lots beginning in January 2021.
Who's Fighting Against the Law?
The suit was filed by the Alliance for Automotive Innovation, a trade group whose members include automakers like BMW, Ferrari, Ford, General Motors, Honda, Hyundai, Jaguar Land Rover, Mazda, Mercedes-Benz and many others. Other members are companies that produce components for vehicle manufacturers like Bosch, Denso, Harman, Infineon, Intel, Luminar, NXP Semiconductors, Panasonic, Sirius XM, and Texas Instruments.
In short, the trade group has just about every large automaker and original equipment manufacturer on board, as well as some self-driving startups.
More than $26.6 million was donated in opposition to the referendum, according to Ballotpedia. This includes $5.5 million by General Motors, $4.5 million by Toyota, $4.5 million by Ford, $3 million by Honda, and $2.4 million by Nissan.
The alliance also reportedly funded ads that ran under a shell corporation called Coalition for Safe and Secure Data using its campaign funding, some of which even suggested that women could be hunted down and sexually attacked using the data that would be made available under the new right to repair regs. The ads were pulled from YouTube almost immediately following the overwhelmingly positive vote in favor of the referendum.
Security Concerns
By December 2020, the alliance was already gearing up to take the passage of the referendum all the way to the top. It filed suit against Massachusetts Attorney General Maura Healey in order to combat the law, stating its passage would require automakers to forego "years of manufacturers' work and billions of dollars" which have already been invested in protecting and securing vehicle data. An extensively redacted and under-seal filing reads:
"Based on the evidence adduced at trial, the Data Law would require manufacturers to render inoperative cybersecurity design elements that they installed on vehicles to meet the requirements of the Clean Air Act and EPA regulations regarding vehicle emissions. Because manufacturers cannot comply with both the Clean Air Act and the Data Law, there is a clear conflict between the federal and state law and the state law must yield."
Specifically, the alliance argues that the Data Law would require automakers to render inoperable certain cybersecurity design elements already installed on vehicles.
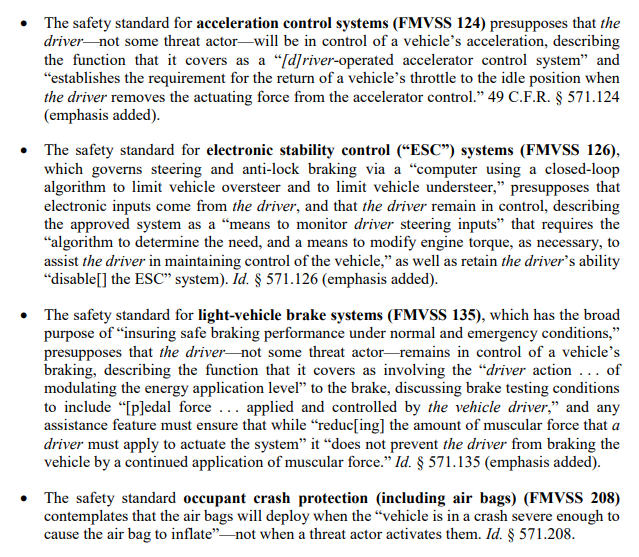
The alliance doubles down by citing the National Traffic and Motor Vehicle Safety Act, indicating that the law's requirement for remote access of vehicle telematics could create a cybersecurity-related safety issue that could require a broad recall of vehicles. Specifically, it cites the “ability to send commands to in-vehicle components if needed for purposes of maintenance, diagnostics, and repair," which it fears would allow "uncontrolled access" to a vehicle's firmware.
Several areas from the NHTSA-issued Federal Motor Vehicle Safety Standards (FMVSS) are also cited, including the requirement for the driver to control the vehicle's acceleration control, electronic stability control, and light-vehicle brake, as well as occupant crash protection systems. The alliance argues that this excludes a potential threat actor from being permitted to take control of a vehicle and that removing the in-place cybersecurity controls would simply permit this.
The Conundrum
Right to repair advocates argue that this case is nothing more than a money grab from automakers who want to protect the dealership model. That notion, which is shared by many enthusiasts, might not be the whole story, of course.
"There is no fundamental difference between the challenges that the farmers are having and the challenges that independent mechanics in Massachusetts are having, or the challenges that we're having like with Apple pairing cameras to iPhones," said Kyle Wiens, the CEO of iFixit, ahead of the referendum's passage. "It is fundamentally the same set of monopolistic tactics, it's the same technical solution."
Make no mistake, I'm absolutely a proponent of the right to repair. The ethics of fixing property that you purchased feels almost like a rudimentary requirement or basic right. Ethics aside, cybersecurity—the point of the argument from the alliance and its member organizations—isn't an open and shut case. The world is becoming increasingly connected and state-sponsored threat actors are more common than ever. That's what makes this particular fight so much more interesting and complex than the legislation enacted almost a decade ago.
The alliance argues that in order to meet the requirements of Massachusetts' Data Law, automakers would need to remove existing cybersecurity safeguards already installed in vehicles. However, the text doesn't go into why these particular safeguards would need to be removed, likely due to the complexity of proprietary business nature of how OEMs achieve security.
That being said, it would be difficult to imagine that an automaker would outright remove in-place logical access controls in its vehicle telematics platform.
Instead, it's much more likely that an automaker would develop other controls which allow access to data applicable to the standard set forth in the referendum and restrict access to the components excluded. That requirement could mean automakers need more time given that some MY2022 vehicles are already on the road.
Automakers likely have already developed components and software responsible for proprietary cybersecurity protection on existing and some next-generation vehicles. Not only would manufacturers need to re-develop these platforms to be compliant with the Data Law, but some may actually need to revisit the existing hardware physically installed in the vehicle.
It's crucial to understand that not all vehicle controls are built like infotainment systems. Many function-critical components rely on Application-Specific Standard Parts (ASSPs) and Application-Specific Integrated Circuits (ASIC) which are programmed to perform very specific and repetitive jobs extremely quickly. It may not be possible to simply reprogram existing hardware to meet the requirements of the new referendum, but instead could require additional or replacement hardware which could incur a significant cost—hence the fight against the legislation.
Nothing Is Secure
Cybersecurity is an uphill battle. No matter how many holes you patch in the ship, there will always be another water leak begging to be found by the right person (or threat actor). And on top of this, the U.S. as a whole has a significant shortage of talent trained in cybersecurity blue-teaming, especially given the diverse skill sets needed for different industries. Even government-backed training exists, such as Purdue's apprenticeship program, in an attempt to fill this void.
Connected vehicles are not exempt from this reality. As four-wheeled computers become the norm in this business, the more serious a cybersecurity threat can become. And in a perfect world, if the automaker could delineate access control at the software level using existing hardware, it still doesn't guarantee immunity from outside threats. If a bad actor can interact with a system remotely or physically, there is always the potential to find a hole.
With physical access to a vehicle, that's possible even now. For example, Comma AI's OpenPilot works in some vehicles by adding an interface between the lane-keeping camera and vehicle body harness to capture CAN packets not present at the OBDII port. Likewise, a security researcher recently responsibly disclosed a vulnerability in Tesla vehicles that allowed a proximity-based attack to execute commands from the vehicle's infotainment system. The vulnerability stemmed from a piece of open-source software that may also be present in vehicles from several other automakers, including GM and Nissan.
As an aside, if you're interested in learning more about these types of risks and attack vectors from an education perspective, The Car Hacker's Handbook is a great place to start.
Does that mean that every vehicle is vulnerable? Yes and no.
If a vulnerability is found, the automaker would (presumably) be responsible for patching it, and the process should be fairly straightforward given that it's always phoning home. But how long is the automaker responsible for updates and software maintenance? Would there be such a thing as End-of-Life or End-of-Support for a connected vehicle's closed-source coding? And what happens if a security vulnerability is found after either of those are reached? Most importantly, who pays for this?
"If allowed to take effect, the Data Law would make serious cyberattacks much more likely and deadly than the attacks on pipelines and meat processers currently in the news," reads another filing in the court case. "To comply, manufacturers must remove or seriously degrade existing cybersecurity controls that help to protect electronic vehicle systems—exposing safety-critical functions to hacks from hostile actors anywhere in the world."
That sentiment is a bit heavy-handed. One could argue that with enough time and money, an automaker could absolutely be timely in its response to such threats. But what about the interim when a zero-day vulnerability is exploited and the worst-case scenario described by lawyers plays out? This type of legislation is still in its infancy and doesn't necessarily cover where an automaker's accountability begins and where its liability ends.
If nothing is secure, does the alliance's argument really matter anyway?
What Next?
It's unclear how the judge will rule on this particular case. It does open the door to a more important discussion on cybersecurity in automobiles, something that's rapidly changing, yet hasn't effectively been addressed in modern vehicle regulations.
The right to repair property that you purchased is something everyone deserves. To close the doors on valuable data is helpful only to those who have the key, and in this case, it certainly isn't the consumer. Could this protection also be safeguarding fleets of vehicles from being abused en masse? Maybe, or maybe not. This may be a case looked back upon years later as one of the first impactful cybersecurity rulings in the automotive industry.
Got a tip or question for the author? Contact them directly: [email protected]